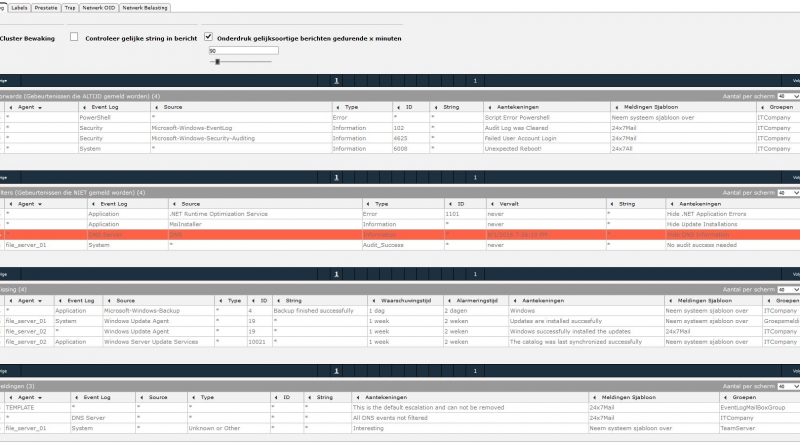
Log File versus Event Log monitoring
The Event Log is a great invention. All it takes is to monitor the complete event log in real time and then read the important messages from it. Sometimes this is more complicated than you think …
Good monitoring helps you with this. By Filtering notifications (omitting), Forwarding (forwarding immediately) and Missing (warning if an event is delayed for too long), and if there are still notifications, you can receive them in a collection box.
Then UNIX / linux, many types and flavors and many log files. This is also sometimes more complicated than you think. Start with knowing what the most important log files are: /var/log/messages;/var/log/auth.log;/var/log/secure;/var/log/boot.log;/var/log/dmesg;/ var / log / kern.log; / var / log / faillog; / var / log / cron; /var/log/yum.log; / var / log / maillog; var / log / httpd /; / var / log / mysqld.log
Have this monitored in real time by the monitoring tool and sound the alarm if certain strings do or do not appear in it and voilá.
Both Operating Systems have their pros and cons, one is no better than the other in my opinion. You can have both under control with proper monitoring and you can also make a mess of both if you do not handle them professionally.
For more information, about Event log Monitoring in the TSMS documentation: https://tsms.nl/doc/EventLog.html