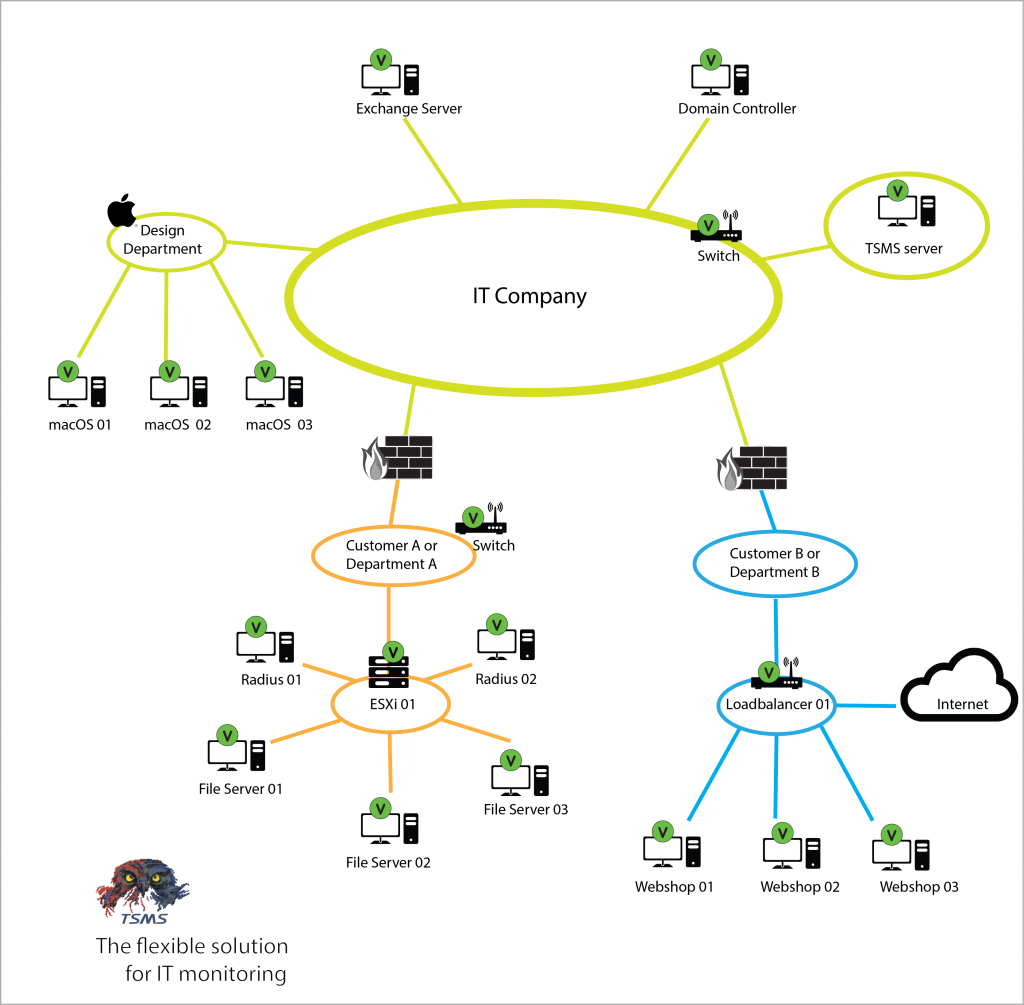
TSMS monitors simply and flexible the complete IT environment. It is crucial to every organization to detect on time any deviations in all the IT systems, devices, networks and applications and prevent precious downtime. Every IT environment can be guarded with TSMS, as long as the devices talk TCP/IP and/or SNMP.
TSMS has been developed by the company Triangle Solutions, a fully independent Dutch software company. In addition to TSMS, Triangle Solutions has also developed VDSS, Data Security. VDSS/TSMS is a client server application with experience in large organizations for over 20 years, with many clients on 1 server.
Many of these larger customers perform standard Security Scans. Company resources such as equipment, networks, data, software and processes are mapped in Security Scans. A risk analysis is performed for each company resource. TSMS/VDSS are regularly included in these tests as part of the monitoring.
With the feedback and advices, we take the appropriate actions. This has ensured, among other things, that the current TSMS meets strict safety measures.
TSMS does not have a so-called “build-in backdoor” account or access to your system without your knowledge.
TCP/IP Connections
Outgoing connection: TSMS Agents are installed on the production systems, which then can be monitored/controlled. Only when needed, the TSMS Agent contacts the TSMS Server directly, using the TCP/IP protocol. By default, port 2345 is used, deviant settings can be set when installing the TSMS software. If desired, you can further secure this connection yourself, for example through a VPN connection.
Incoming connection: The TSMS Server can also connect to the TSMS Agent, but this is not necessary and can be switched off. This connection is made via the TSMS Sysinfo functionality. By default, port 2346 is used, also this port can be adjusted when installing the TSMS software.
E-mail agent: In addition, there are also more and more environments where no TCP/IP connection is allowed anymore, not only for incoming traffic, but also outgoing traffic. In that case, TSMS can provide an email Agent, which will send the encrypted TCP/IP packets via a mail connection to the TSMS Server. This is available on request and is not standard in the current version of TSMS.
For years, we have been providing solutions for monitoring in hospitals, where MRI systems are located in a “closed” environment. These systems are monitored with an email Agent.
Protocols and Encryption
Security by Design: The TSMS Server and Agents communicate via same
standards, a protocol is used developed in-house by Triangle Solutions.
This set of rules and procedures is necessary for communication between
the TSMS Server and the Agents.
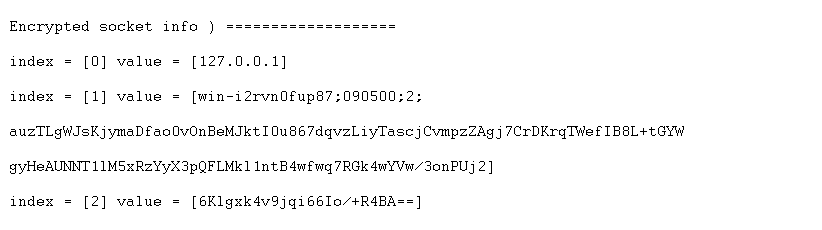
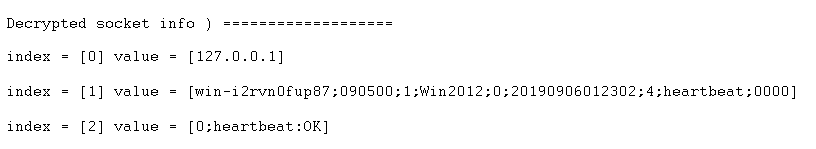
This TSMS protocol consists of commands, to understand each other, but in addition, data also crosses the line. The data sent over the line by TSMS contains as little sensitive data as possible and is kept as small as possible. Building the concept, this was taken into account and only significant information is sent over the network.
Security: Sniffing, for example, checks out the data from the line and show the protocol. To prevent this, the following security features are built in.
- Handshaking protocol: checks the data using control signals between the TSMS Server and Agent and improves the messaging between the systems.
- Encryption: TSMS uses the rule of two for encrypting their data between TSMS Server and Agents. The Rule of Two is a data security principle of the NSA’s Commercial Solutions for Classified Program (CSfC). It specifies two completely independent layers of cryptography to protect data. TSMS first of all uses AES, an official encryption standard specified by the National Institute of Standards and Technology (NIST). AES encryption is used worldwide by many different organizations, for instance governments, banks and developers of security software
Each TSMS Agent sends a Diffie-Hellman Key after installation to the TSMS server for its first time login. This means that each connection is encrypted differently.
In addition, TSMS adds an extra layer of encryption on top. This provides extra security when a leak is found in AES.
TSMS Agent
Performance: The TSMS Agent takes on average 40 MB of disk space and is installed separately from your system in its own directory. The CPU load of a TSMS agent is approximately 1 to 2% and will use an average of 30 MB of memory.
