First Kaseya, SolarWinds and now Zabbix…
After the Kaseya hack, then the SolarWinds hack, now it’s Zabbix’s turn. Vulnerable By Design I call these kinds of applications.
Which supplier with which toolings do you purchase as an end customer/entrepreneur. A few simple questions are enough and a few extra lines in the contract are often more than enough. Good agreements about who and what is present on your network, how these accesses are established and who/what can/may be involved with your data are some important issues.
Suppliers with a link to the “back doors” of their own delivered goods. Monitoring tools that automatically configure the monitoring and get automatic updates from the suppliers internet sites… Free-/shareware tools, do you remember which code is running and who is responsible for it?
Of course convenience serves people and therefore also… the hackers. Supply chain hacking is currently widely used by hackers.
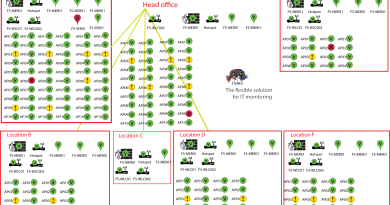
With TSMS and VDSS we provide a modern, accurate and as safe as possible monitoring and data security solution. So no backdoors, no automatic upgrades, no internet connection required, but of course modern suitable for on-premises and cloud, agents that can only communicate outgoing and if there is no direct outgoing connection, the packets can even be routed out of the network via email. So we continue to build, of course affordable and implementable for small and large!
Read more about vulnerabilities in Zabbix servers