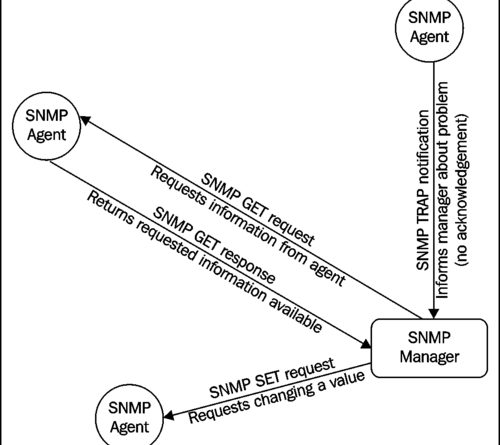
SNMP
In the early years of IT, SNMP (Simple Network Management Protocol) was developed to simplify the management and data collection of network devices. Due to the ease of use, manufacturers of network equipment started to implement SNMP in all their hardware. SNMP was enabled on all kinds of equipment such as: switches, routers, firewalls, network printers and even on file servers. Previously, SNMP was often switched on automatically, today it is increasingly being switched off due to security.
Security SNMP
Because it was made for management, no attention was paid to security in the first versions. In SNMP 1.0 and 2.0, communication is not encrypted and sent as plain text. In SNMP 3.0 this issue has been resolved, the management functions have been improved and you can set different user levels.
However, manufacturers usually still ship products with built-in standard community strings that are known in the hacker community. So although SNMP 3.0 offers many security benefits over previous implementations, it does not protect against danger if it is not implemented correctly.
SNMP as a threat
This lack of protection is deteriorated by the fact that SNMP is often performed on devices located on the edge of the network. Routers, which often is placed outside a firewall, perform SNMP. Other SNMP enabled devices that could be nightmare scenarios include switches, printers, UPS’s and networked medical devices.To make clear how big the problem is, the SANS (www.sans.org) institute sees it as one of the top 10 internet threats. Computer Emergency Readiness Team of the US government (US-CERT) issued another warning in 2017 and DDoS attacks have revealed that hackers are also abusing snmp to reinforce their attack
Conclusion
SNMP can still help network managers manage large networks efficiently. However, be aware of the risks and ensure that the security is high. This can be done by using SNMP 3.0, configuring at the highest security level, no standard passwords and using local SNMP, but sending encrypted remotely.If you think you are not using SNMP, it is advisable to take a few minutes to investigate whether this is indeed the case. Because the best way to avoid the SNMP risk is to disable the service.